ValleyRAT Attacking Org’s Accounting Department With New Delivery Techniques
Researchers unveiled a sophisticated malware campaign in a recent cybersecurity alert involving ValleyRAT, a Remote Access Trojan (RAT) frequently linked to the Silver Fox APT group. This threat has evolved with new delivery techniques, targeting key roles within organizations, particularly in finance and accounting departments. The attackers exploit vulnerabilities in legitimate software and use advanced […] The post ValleyRAT Attacking Org’s Accounting Department With New Delivery Techniques appeared first on Cyber Security News.

Researchers unveiled a sophisticated malware campaign in a recent cybersecurity alert involving ValleyRAT, a Remote Access Trojan (RAT) frequently linked to the Silver Fox APT group.
This threat has evolved with new delivery techniques, targeting key roles within organizations, particularly in finance and accounting departments.
The attackers exploit vulnerabilities in legitimate software and use advanced tactics to evade detection.
ValleyRAT is a C++-based RAT that offers functionalities typical of basic RATs, including capturing input and injecting actions.
Morphisec Labs analysts noted that it hooks functions like AmsiScanString, AmsiScanBuffer, and EtwEventWrite to bypass security mechanisms such as AMSI and ETW, allowing it to remain undetected.
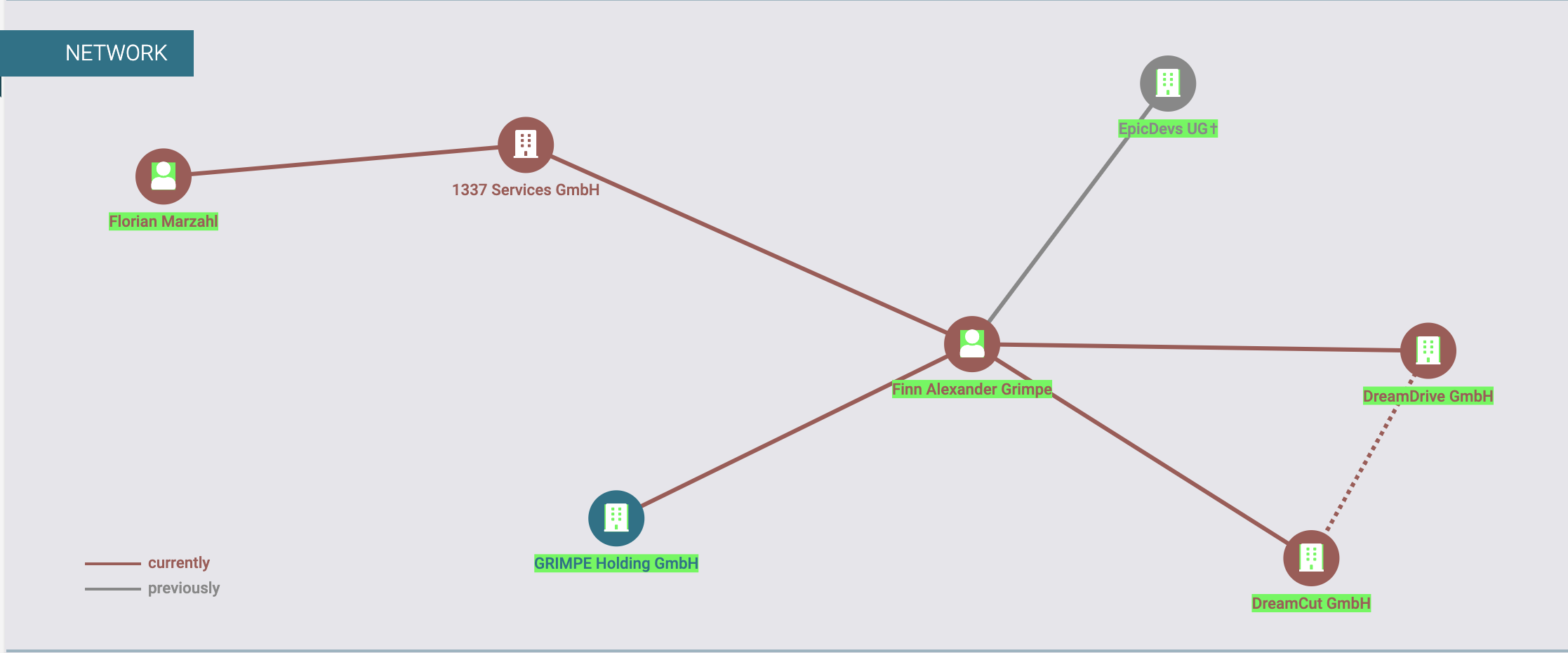
Infection Chain
The infection begins when a user downloads a fake Chrome browser from a phishing website, such as https://anizom[.]com/.
Another phishing site, https://karlost[.]club/, impersonates a Chinese telecom company named “Karlos.” Users are tricked into downloading a Setup.zip file containing Setup.exe, which requests administrator privileges upon execution.
.webp)
# Example of Setup.exe's actions
- Validates administrator privileges
- Checks the operating system type
- Downloads additional files:
- sscronet.dll
- douyin.exe
- mpclient.dat
- tier0.dll.webp)
While the payload execution involves:-
- sscronet.dll: This DLL is loaded into memory using
LoadLibrary. It callsCronet_UrlRequest_StartandCronet_UrlRequest_Readto execute malicious code withinsvchost.exe, acting as a monitoring mechanism to terminate excluded processes. - douyin.exe: Exploited using DLL side-loading, where a malicious DLL is placed alongside Douyin.exe (the Chinese version of TikTok).
- tier0.dll: Used to check for
nslookupprocesses, which can act as a mutex to avoid detection.
ValleyRAT achieves persistence by adding a registry entry under “Software\Microsoft\Windows\CurrentVersion\Run.”
.webp)
It also checks for VMware environments to evade detection in virtual machines. If not running in a VM, it attempts to connect to www.baidu.com for network communication checks.
ValleyRAT initializes C2 IP addresses and ports within its code. Commands include plugin cleanup, process list retrieval, and executing DLLs.
# Example C2 Commands
0x00: Plugin cleanup and get system process list.
0x01: Reply with STRUCT_PACKET_0x02 structure for anti-bot verification.
0x02: Drops and executes a DLL.To protect against ValleyRAT, organizations should employ proactive cybersecurity measures that will help to stop the attacks at an early stage by preventing exploitation rather than relying solely on detection.
Organizations must stay vigilant and adapt their defenses to counter sophisticated malware attacks.
Indicators of Compromise (IOCs)
- C2 IPs: 149.115.250.19, 149.115.052.91, 8.217.244.40, etc.
- Phishing Sites:
https://anizom[.]com/,https://karlost[.]club/ - File Hashes: Available in the Morphisec report for specific files like
Setup.exeandsscronet.dll.
Are you from SOC/DFIR Teams? – Analyse Malware Files & Links with ANY.RUN Sandox -> Start Now for Free.
The post ValleyRAT Attacking Org’s Accounting Department With New Delivery Techniques appeared first on Cyber Security News.