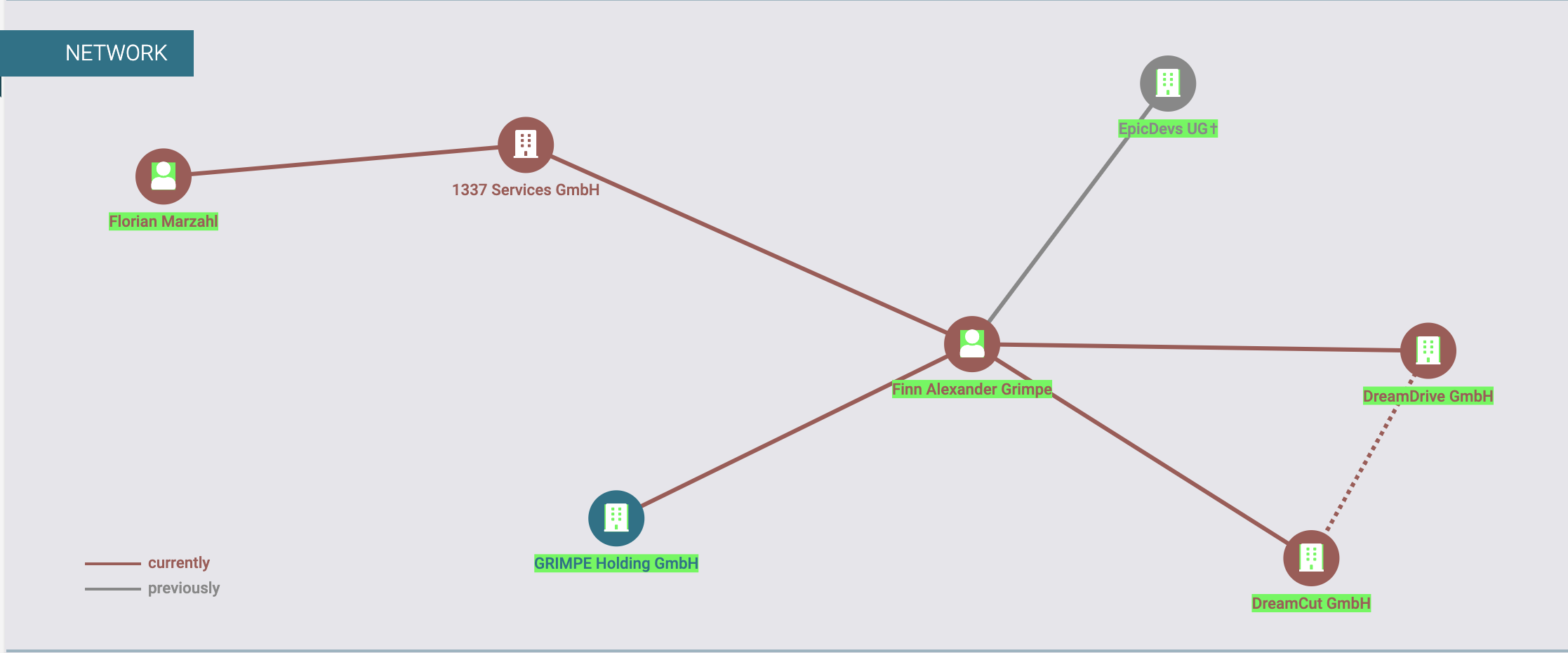
Critical Microsoft Accounts Authentication Bypass Vulnerability Let Attackers Gain Remote Access
Microsoft has issued a security advisory for CVE-2025-21396, a critical authentication bypass vulnerability that could allow attackers to spoof credentials and gain unauthorized access to Microsoft accounts. Cybersecurity experts are urging users and organizations to swiftly address this issue by applying relevant updates and following Microsoft’s guidance. The vulnerability is linked to CWE-290, Authentication Bypass […] The post Critical Microsoft Accounts Authentication Bypass Vulnerability Let Attackers Gain Remote Access appeared first on Cyber Security News.

Microsoft has issued a security advisory for CVE-2025-21396, a critical authentication bypass vulnerability that could allow attackers to spoof credentials and gain unauthorized access to Microsoft accounts.
Cybersecurity experts are urging users and organizations to swiftly address this issue by applying relevant updates and following Microsoft’s guidance.
The vulnerability is linked to CWE-290, Authentication Bypass by Spoofing, a well-documented weakness that affects authentication mechanisms relying on insufficient or flawed validation methods.
This flaw may particularly affect systems where trust is placed on sources such as IP addresses or DNS names, both of which are susceptible to manipulation by attackers.
Technical Details: CVE-2025-21396
Authentication Bypass by Spoofing defines a scenario where an attacker can trick the system into accepting them as an authenticated user by presenting false credentials or manipulating authentication parameters. Below are the technical specifics:
Nature of the Vulnerability
The issue arises from improperly designed authentication mechanisms that fail to robustly validate incoming requests. Exploits may involve:
- IP Spoofing: The attacker forges their source IP address to impersonate a trusted system.
- DNS Spoofing: Poisoning the DNS cache to present an attacker-controlled domain as legitimate.
- Malformed or Manipulated Requests: Exploiting weak validation logic in application-layer protocols.
Attack Vector Examples
Attackers leveraging this vulnerability might exploit:
- Use of IP address-based source validation.
Example in Java:
String sourceIP = request.getRemoteAddr();
if (sourceIP != null && sourceIP.equals(APPROVED_IP)) {
authenticated = true;
} In this case, an attacker spoofing the IP address could bypass authentication.
- DNS-based host verification is where the attacker manipulates DNS responses to create a false sense of trust.
Example in C:
struct hostent *hp;
struct in_addr myaddr;
char *tHost = "trustme.example.com";
myaddr.s_addr = inet_addr(ip_addr_string);
hp = gethostbyaddr((char *)&myaddr, sizeof(struct in_addr), AF_INET);
if (hp && !strncmp(hp->h_name, tHost, sizeof(tHost))) {
trusted = true;
}An attacker poisoning the DNS cache could exploit this to impersonate a trusted source.
Due to the ease of performing IP spoofing or DNS cache poisoning in certain scenarios, this vulnerability is categorized as having a high likelihood of exploitation.
Guidance and Mitigation
Microsoft has released patches addressing the root cause of CVE-2025-21396. Customers are advised to take the following preventive steps:
- Apply Security Updates: Regularly update operating systems and software to the latest versions. Check the Microsoft Security Update Guide for specific instructions.
- Adopt Stronger Authentication Mechanisms: Avoid relying solely on IP addresses or DNS names for trust mechanisms. Instead, use secure alternatives such as, Multifactor authentication (MFA), Cryptographic tokens for identity validation, Mutual TLS for secure connections.
- Monitor Networks for Anomalies: Set up intrusion detection systems (IDS) to identify spoofed packets or unusual DNS behavior.
- Harden DNS Infrastructure: Implement DNSSEC to mitigate DNS spoofing risks.
- Enable Logging: Maintain detailed logs of authentication attempts for forensic analysis in case of exploitation attempts.
“Microsoft has fully mitigated this vulnerability. There is no action for users of this service to take. The purpose of this CVE is to provide further transparency.” Microsoft statement.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The post Critical Microsoft Accounts Authentication Bypass Vulnerability Let Attackers Gain Remote Access appeared first on Cyber Security News.