New Android Malware Mimics Chat App to Steal Sensitive Data
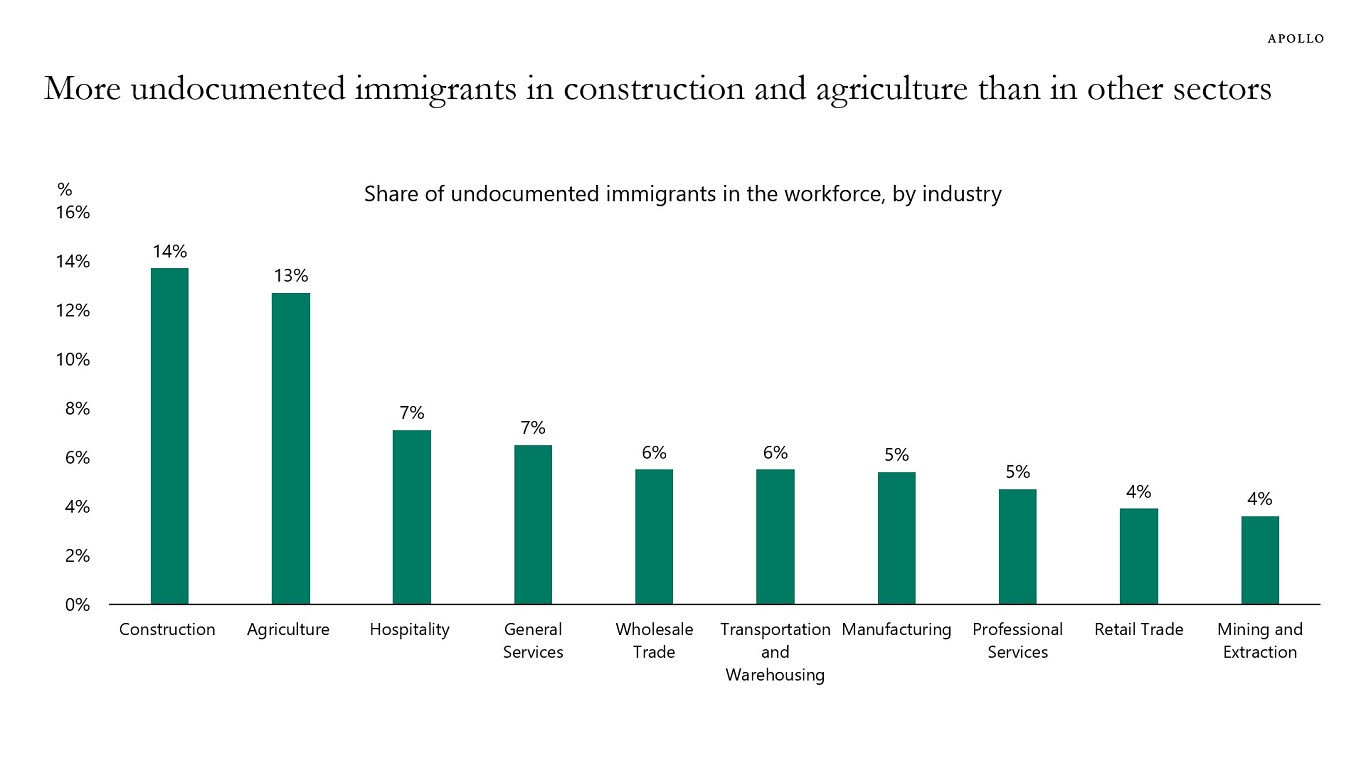
A sophisticated Android malware campaign targeting users in South Asia, particularly in the Kashmir region of India has been recently uncovered by the cybersecurity researchers at Cyfirma. The malware, disguised as a chat application called “Tanzeem,” is attributed to the notorious APT group known as ‘DONOT,’ which is believed to serve Indian national interests. The […] The post New Android Malware Mimics Chat App to Steal Sensitive Data appeared first on Cyber Security News.

A sophisticated Android malware campaign targeting users in South Asia, particularly in the Kashmir region of India has been recently uncovered by the cybersecurity researchers at Cyfirma.
The malware, disguised as a chat application called “Tanzeem,” is attributed to the notorious APT group known as ‘DONOT,’ which is believed to serve Indian national interests.
.webp)
The malicious app, discovered by CYFIRMA’s research team, poses as a legitimate chat platform but ceases to function once installed.
.webp)
Instead, it requests extensive permissions to access sensitive user data and device functions. Two nearly identical samples were collected in October and December 2024, indicating an ongoing campaign.
“Tanzeem,” which translates to “organization” in Urdu, is a term often associated with terrorist groups and law enforcement agencies in the region.
Analysts at Cyfirma noted that this naming suggests the malware is designed to target specific individuals or groups both within and outside India.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Technical Analysis
The malware leverages OneSignal, a popular customer engagement platform, in an unprecedented way for this APT group.
Researchers believe the attackers are misusing OneSignal to deliver phishing links through push notifications, enhancing the malware’s persistence on infected devices.
Technical analysis reveals that the malware requests dangerous permissions, including access to call logs, contacts, SMS messages, file storage, and precise location data.
.webp)
It also seeks permission to extract emails and usernames used for logging into various internet platforms.
The malware employs sophisticated evasion techniques, including obfuscation to hide malicious code within the APK. It can enumerate files and directories, capture keystrokes, collect system information, and even record the device’s screen.
CYFIRMA researchers identified several indicators of compromise, including the SHA-256 hash 8689D59AAC223219E0FDB7886BE289A9536817EB6711089B5DD099A1E580F8E4 for the malware file. Command and control domains such as toolgpt[.]buzz and updash[.]info were also uncovered.
.webp)
The DONOT APT group has a history of targeting government and military organizations in South Asia. This latest campaign demonstrates their evolving tactics and persistent focus on the region.
Cybersecurity experts warn that the group is likely to continue refining their methods to maintain persistence in future attacks.
Users are advised to exercise caution when installing new apps, especially those requesting extensive permissions.
Besides this, the organizations in the targeted regions are also advised to remain vigilant and implement robust security measures to protect against this evolving threat.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
The post New Android Malware Mimics Chat App to Steal Sensitive Data appeared first on Cyber Security News.