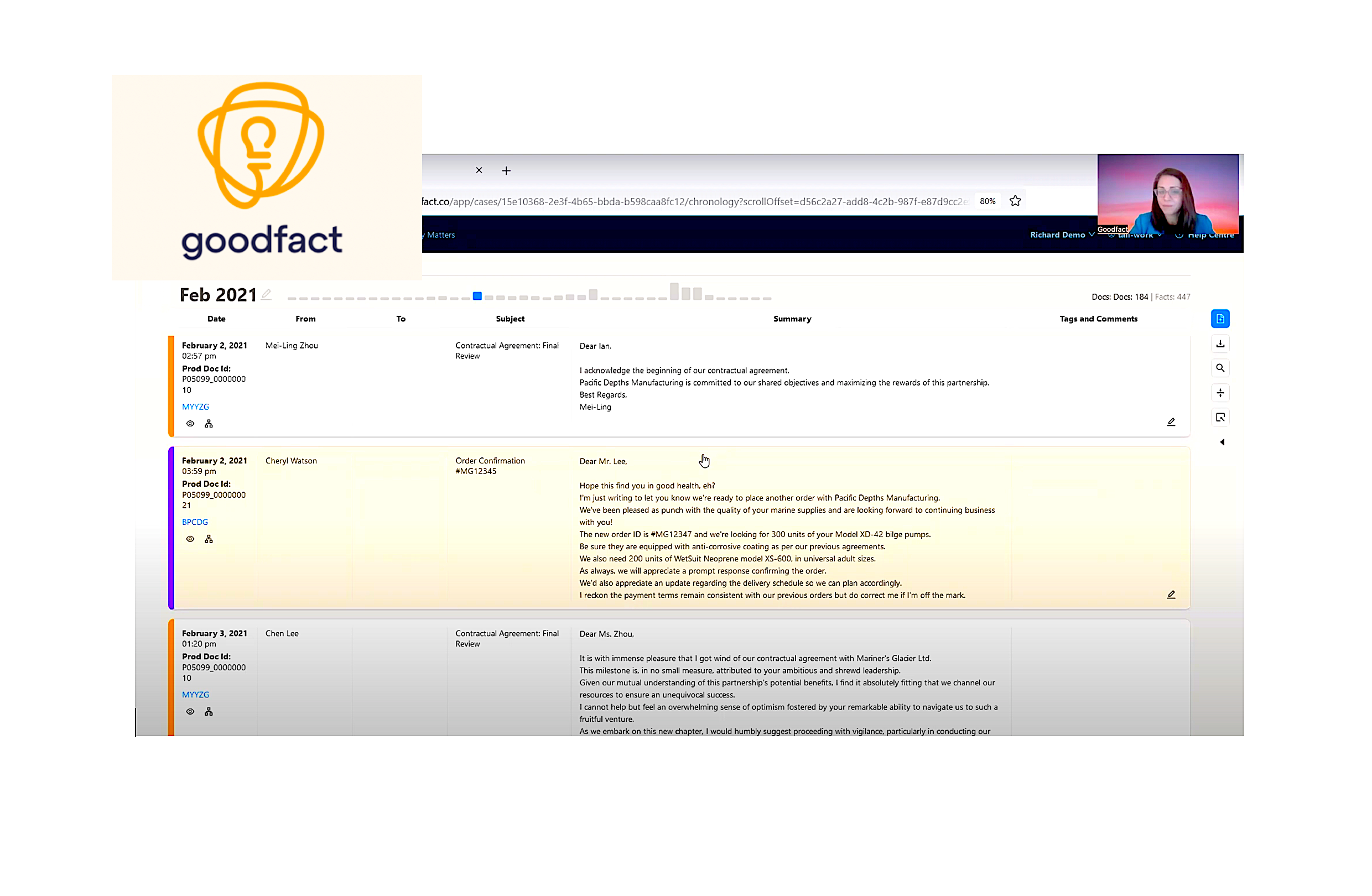
Attackers Exploit IBM i Access Client Solutions on Windows 11 To Steal Passwords
A recent investigation has revealed that attackers are exploiting vulnerabilities in IBM i Access Client Solutions (ACS) to steal Windows user credentials. This alarming discovery highlights the risks associated with the WINLOGON authentication mode, which IBM recently deprecated due to compatibility issues with Windows 11’s Local Security Authority (LSA) Protection. IBM ACS is a widely […] The post Attackers Exploit IBM i Access Client Solutions on Windows 11 To Steal Passwords appeared first on Cyber Security News.

A recent investigation has revealed that attackers are exploiting vulnerabilities in IBM i Access Client Solutions (ACS) to steal Windows user credentials.
This alarming discovery highlights the risks associated with the WINLOGON authentication mode, which IBM recently deprecated due to compatibility issues with Windows 11’s Local Security Authority (LSA) Protection.
IBM ACS is a widely used tool for managing IBM i systems. It offers various authentication methods, including WINLOGON, which allows users to log in using their Windows credentials without additional prompts.
However, the Windows 11 24H2 update introduced LSA Protection, a security feature designed to safeguard sensitive credentials from unauthorized access. This update rendered the WINLOGON mode incompatible, as noted in IBM’s support documentation.
LSA Protection is crucial for preventing credential theft techniques like those employed by the infamous Mimikatz tool, which extracts secrets from the LSASS.exe process.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
While LSA aims to fortify credential security, its interplay with third-party software like IBM ACS has created new attack surfaces.
Exploitation Details
Silent Signal researchers discovered that IBM ACS’s *WINLOGON* feature interacts with Windows’ Network Provider DLLs, which are loaded during user logins via the `mpnotify.exe` process.
These DLLs receive plaintext credentials through a callback function, making them a prime target for attackers.
By manipulating the Windows Registry key responsible for Network Provider order (`HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order`), attackers can insert malicious DLLs into the login process.

These rogue DLLs can intercept plaintext Windows passwords during login, enabling credential harvesting. The issue is exacerbated by IBM ACS’s handling of these credentials.
To facilitate seamless connections to remote IBM i systems, ACS stores plaintext passwords in the Windows Registry under a weakly obfuscated value.
This design flaw allows attackers with local access to decode and retrieve stored credentials.
This vulnerability isn’t entirely new. A similar issue was reported in 2016 when Tenable researchers identified weak obfuscation in IBM System i Navigator’s password storage mechanism.
Despite this early warning, IBM continued supporting WINLOGON until late 2024, when it began phasing out the feature due to mounting security concerns.
The delayed response raises questions about why such a critical vulnerability persisted for nearly a decade before being addressed comprehensively. Even now, users relying on older ACS versions or configurations may remain exposed.
Mitigation And Recommendations
IBM has advised users to transition away from *WINLOGON* authentication and adopt alternative methods such as:-
Default User Profiles: Users are prompted for their password only once per session, with credentials cached temporarily.
Kerberos Authentication: A more secure but complex setup requiring proper configuration.
Other Tools: Options like `cwblogon` or `.netrc` files can be used but carry risks if not implemented securely. Additionally, administrators should review and tighten access controls on systems running IBM ACS. Monitoring registry changes and auditing DLL loads can help detect suspicious activity.
This case underscores the importance of proactive vulnerability management in enterprise software. As platforms like Windows evolve with enhanced security features, legacy software must adapt swiftly to avoid becoming attack vectors.
For organizations using IBM i systems, this incident serves as a wake-up call to prioritize security updates and reassess reliance on outdated authentication mechanisms.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
The post Attackers Exploit IBM i Access Client Solutions on Windows 11 To Steal Passwords appeared first on Cyber Security News.
What's Your Reaction?


















![[FREE EBOOKS] Hacking and Securityy, The Kubernetes Book & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


















![AI in elementary and middle schools [NAESP]](https://dangerouslyirrelevant.org/wp-content/uploads/2025/01/NAESP-Logo-Square-1.jpg)








































